Sudipta Chattopadhyay, Matheus E. Garbelini and Chundong Wang from Singapore University of Technology and Design has first discovered this bug and reported to respective vendors for a fix. And after 90-day responsible disclosure period, they’ve now published how this can affect the vulnerable devices. The flaw is associated with the BLE tech. Bluetooth Low Energy (BLE) is a tech came as Bluetooth 4.0 in 2011 and has been devised into many devices ever since. This technology takes less energy as it stays in sleep mode most of the time and wakes up when the connection is established. This tech is primarily used by most of the smart wearables makers and other utility instruments.
Impacted Vendors and Products
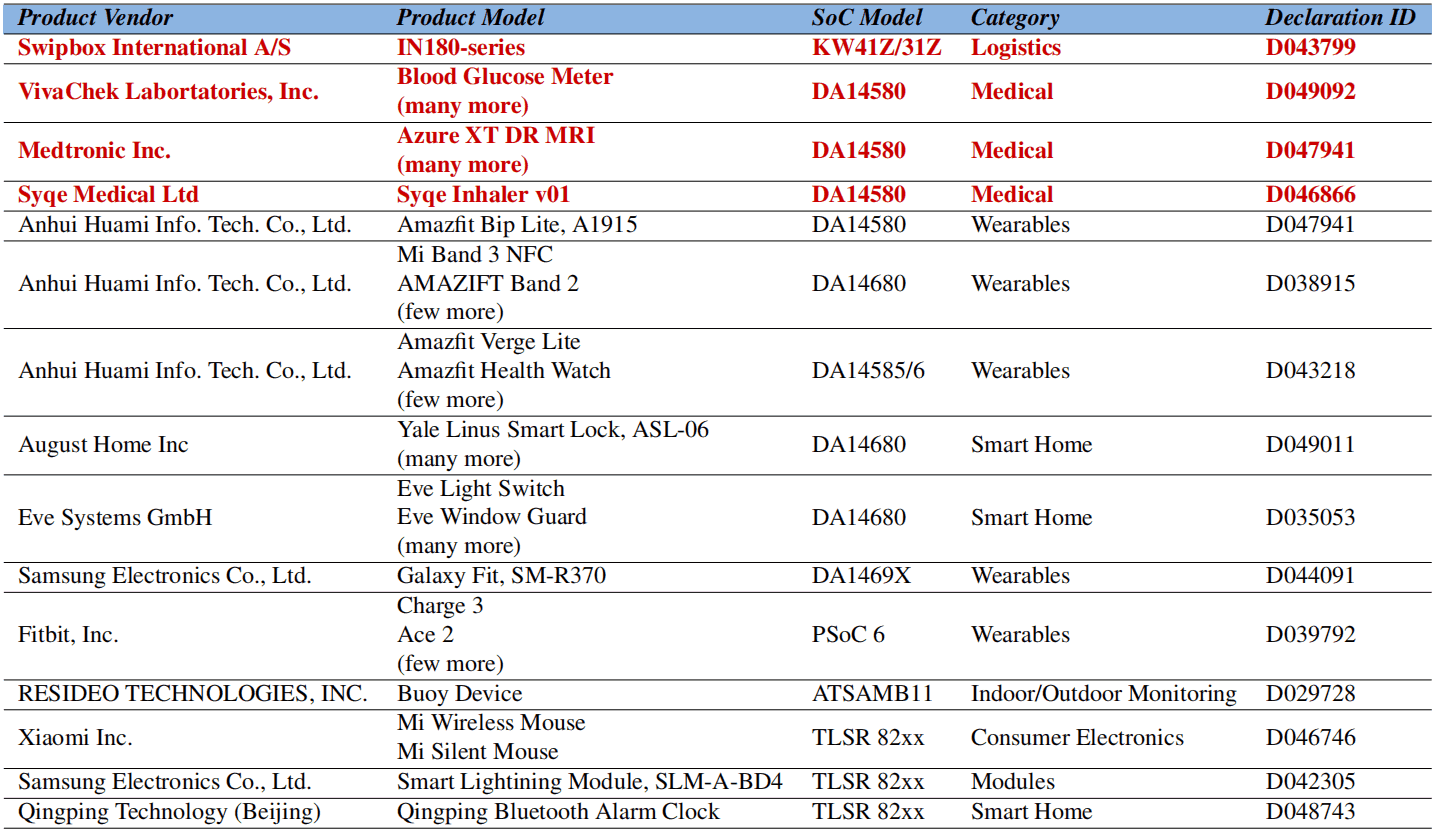
Vendors as NXP, Cypress, Texas Instruments, Dialog Semiconductors, Microchip, Telink Semiconductor and STMicroelectronics, who has their system-on-chip integrated with BLE are affected by SweynTooth. While other vendors are vulnerable too as having this bug. An attacker being in Bluetooth range can leverage this bug to crash the device, bypass BLE pairing and may access unauthorized functions. The group has even tried on few devices to check the credibility of their findings. Most of the devices from Eve smart systems, eGee Touch smart lock, August Smart Lock, CubiTag tracker for lost items and even Fitbit Inspire smartwatch are vulnerable. The attacker would try methods like Zero LTK installation, Link layer length overflow, Link Layer LLOD deadlock, Truncated L2CAP etc to exploit the bugged device. Though this flaw doesn’t seem to be that effective, it’s intimidating when healthcare systems are using this bugged feature. Devices as Syqe Inhaler from Syqe Medical, Azure XT DR MRI from Medtronic, and Blood Glucose Meter from VivaCheck Laboratories found to be impacted by SweynTooth. Other products of these vendors too are vulnerable. Via BleepingComputer